How to Setup Response Pages in VWire Mode
Labels:
Overview
This document will walkthrough the basic steps needed to setup and demonstrate Application Block Pages and URL filtering pages while the Palo Alto Networks firewall is in VWire mode.
Note: Do not use Chrome to test these pages. Chrome will force many connections to SSL even if choosing non-SSL traffic, because of this decryption will need setup due to SSL errors introduced.
Additional information can be found in the following article: https://live.paloaltonetworks.com/docs/DOC-3496
Steps
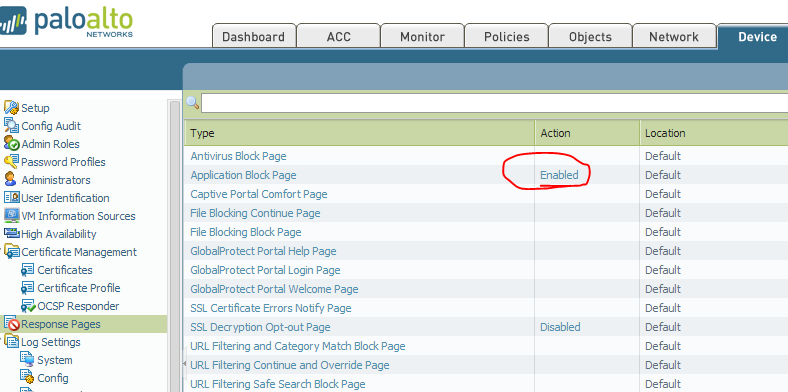
- From the WebGUI, enable the Application Block Page in Device > Response Pages > Action Enable:
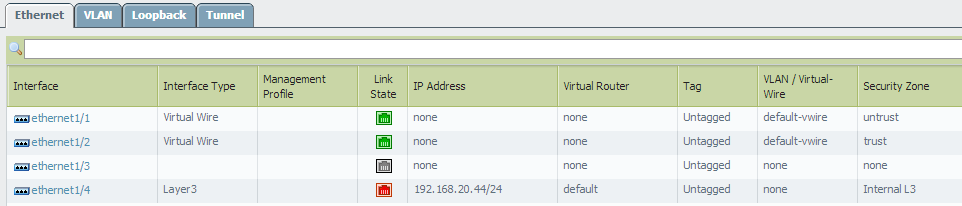
- Verify the VWire in Network > Interfaces > Ethernet is being used:
- Create URL filtering profiles. For example, the following profile will look for Social-Networking URLs and present a Continue page to not only monitor, but also change user behavior.
This is done by going to: Object > Security Profiles > URL Filtering: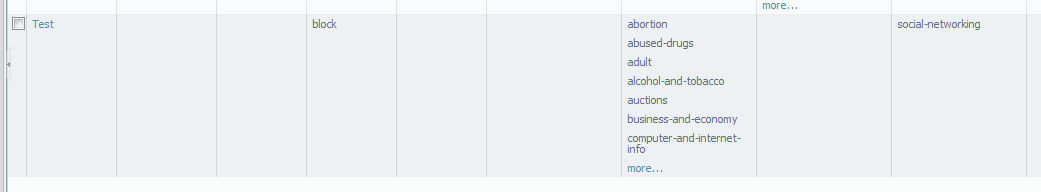
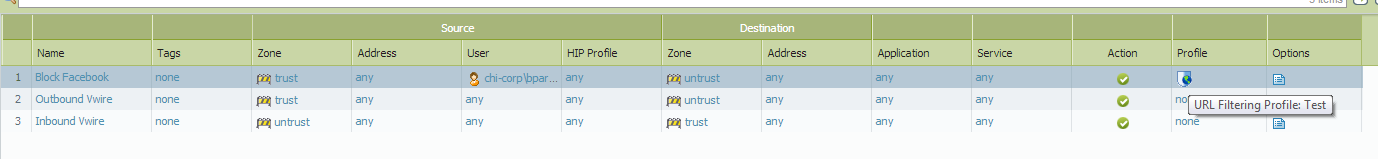
- Create security policies to use the URL Profile in Policies > Security. The following example policy will match all traffic from 'inside(trust) to outside(untrust) interfaces' and match the Active Directory username. It then has the URL filter policy created above applied:
- Commit
- The results are as follows:
From Firefox to http://facebook.com with URL Filtering no decryption: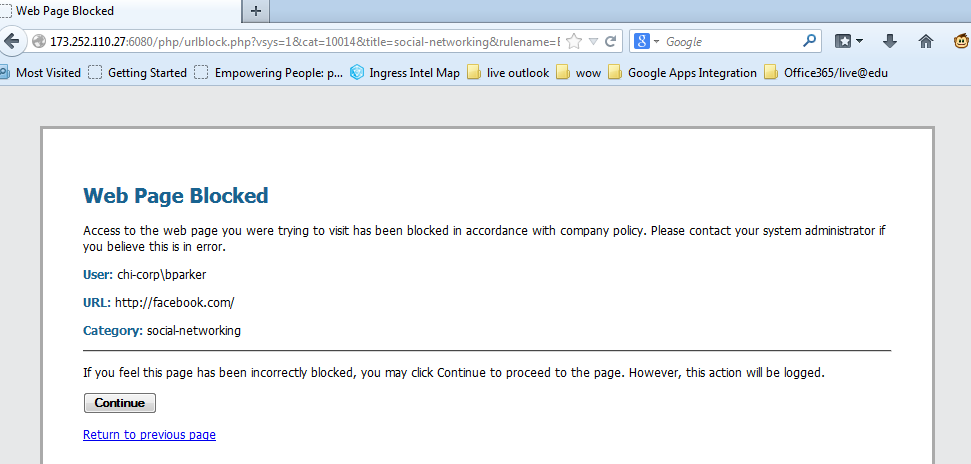
For https://facebook.com in Firefox with URL Filtering no decryption: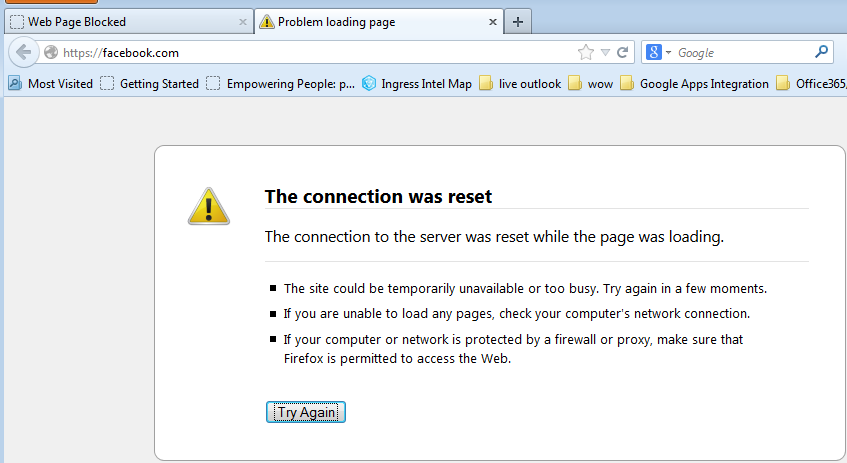
For https://facebook.com in Chrome with URL filtering no decryption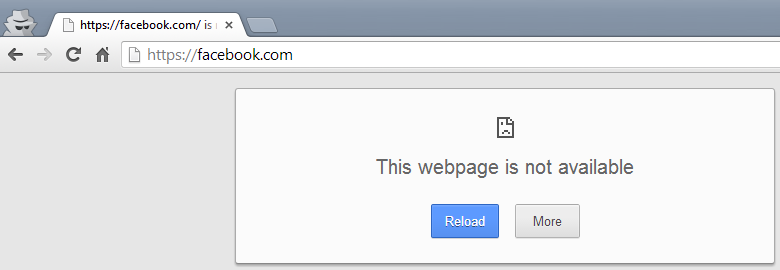
For Application Blocking instead of URL Filtering Block Pages
- Change the security policy to the following:
Remove the URL Profile, add Facebook as an application, change service to application-default, and set the action to Deny: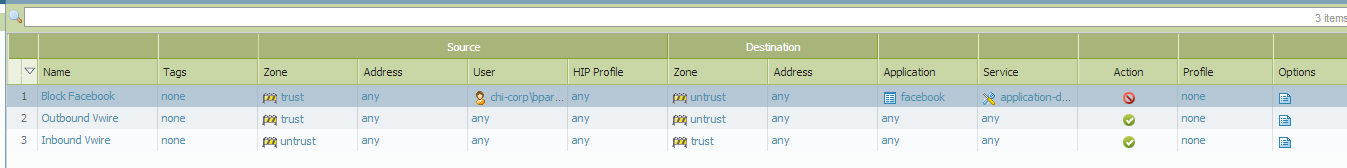
- Commit
- Test
Results:
In Firefox to http://facebook.com with Application denied, no decryption: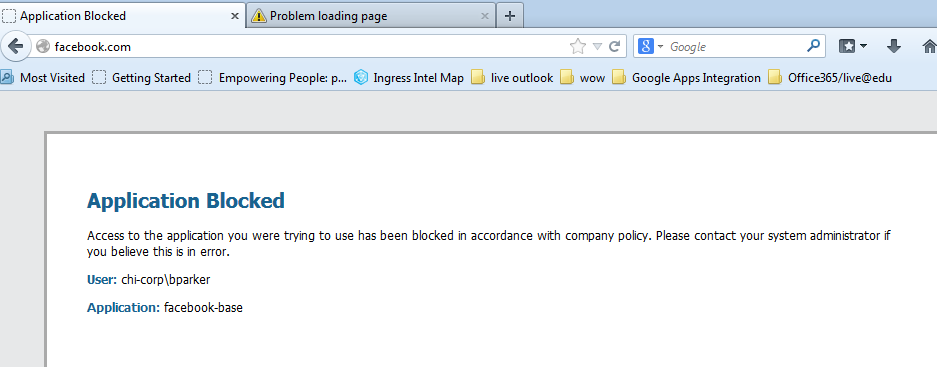
In Chrome to http://facebook.com with Application denied, no decryption: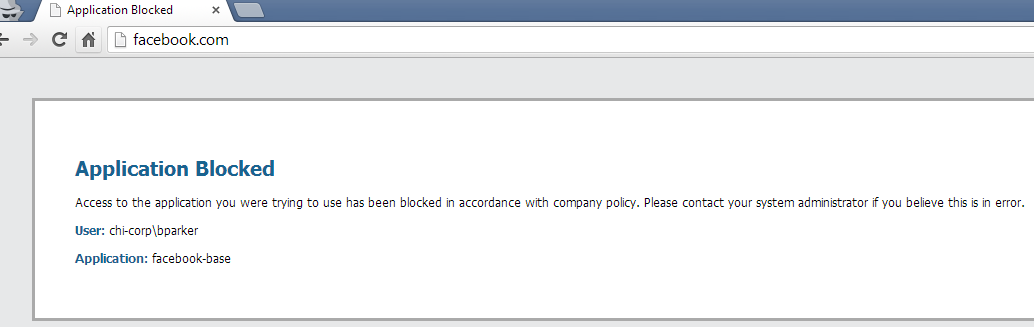
In Firefox to https://facebook.com with Application denied, no decryption: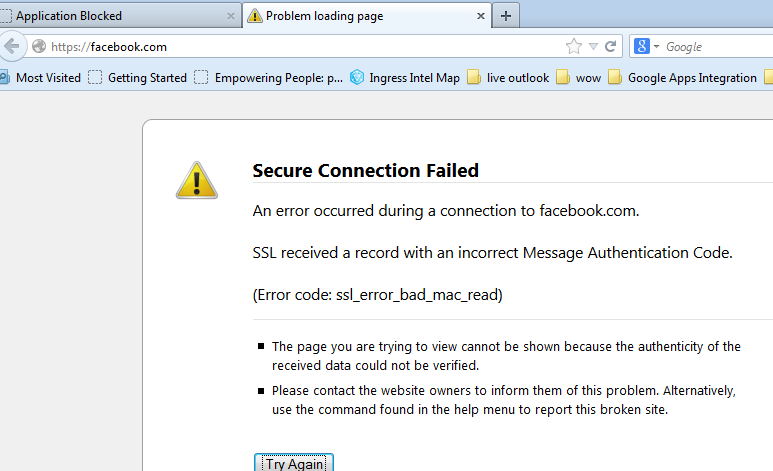
In Chrome to https://facebook.com with Application denied, no decryption: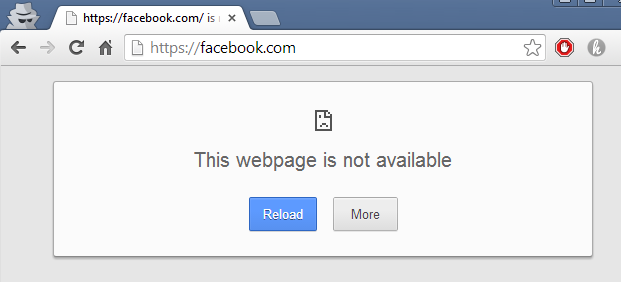
Enabling Basic Forward Proxy or Outbound Decryption, using a Self Signed Certificate
- From the WebGUI, go to Device > Certificate Management > Certificates > Generate. Create a new self-signed certificate that is a certificate authority. Click Generate and receive the following message:
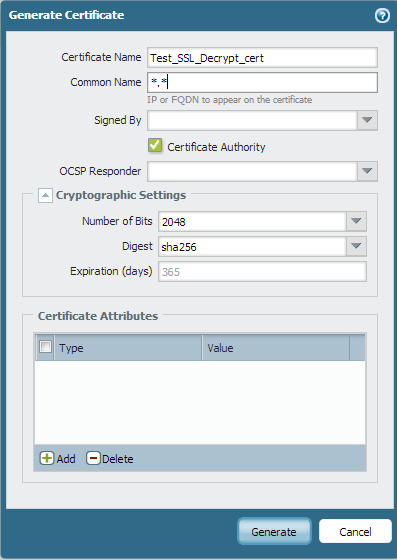
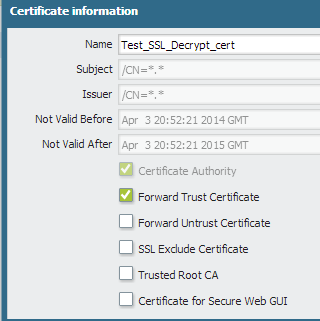
- Click on the certificate to open it and select Forward Trust Certificate:
- Go to Policies > Decryption and create a new decryption policy to match the following:
Source zone = Trust
Source user = AD user
Destination Zone = Untrust
Action = Decrypt
Type = ssl-forward-proxy
- Commit
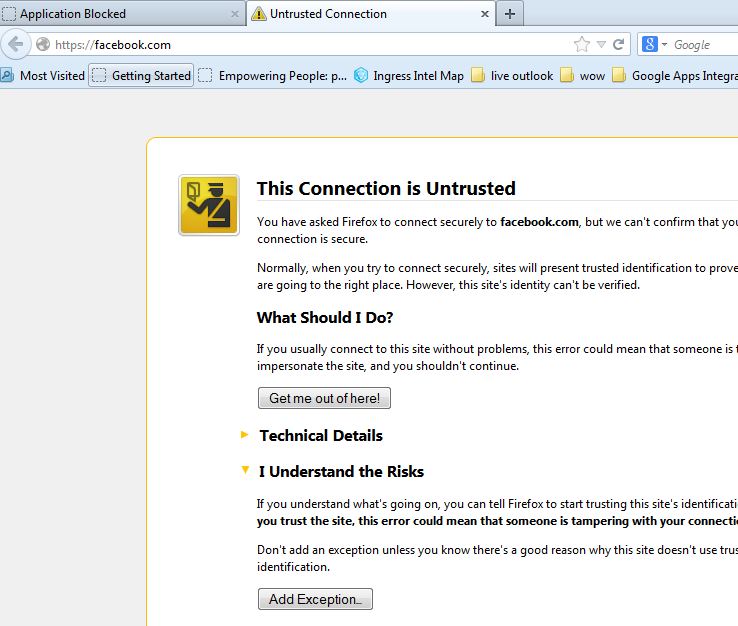
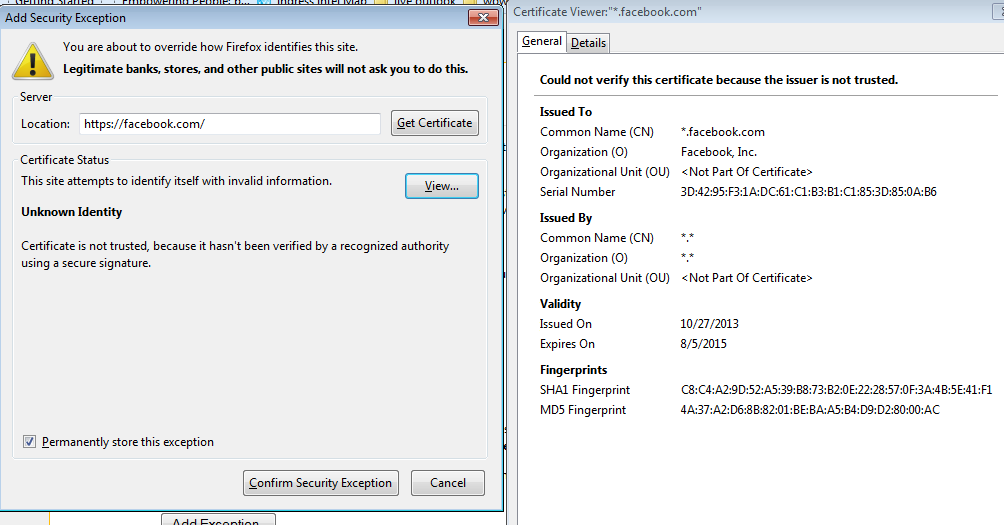
Test Application Block PagesIn Firefox: Note the connection is untrusted, because it has not been added to the Palo Alto Networks self-signed certificate to the computer and browsers root folder. Follow the steps below to add an exception:
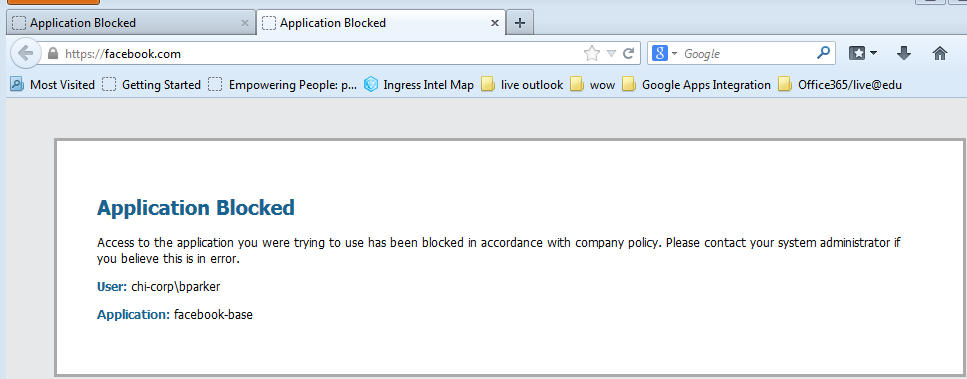



In Chrome: Perform the same process as in Firefox:
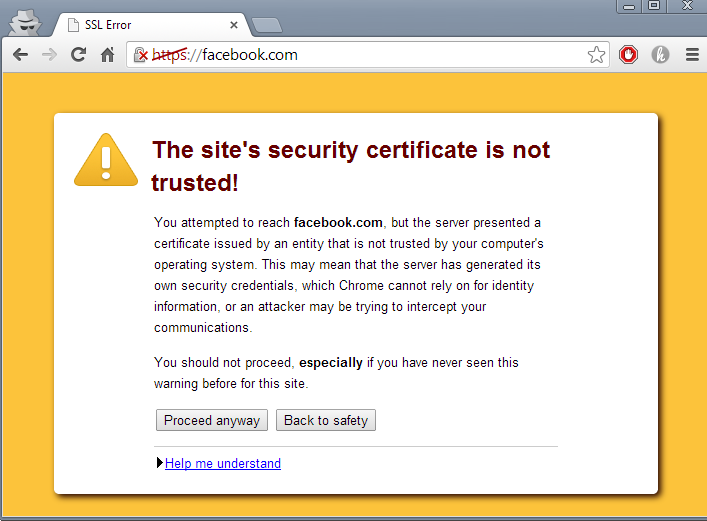

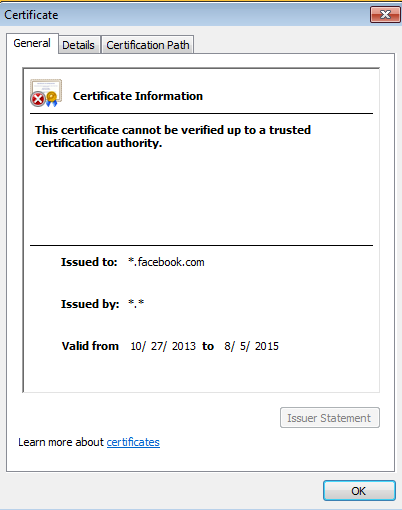
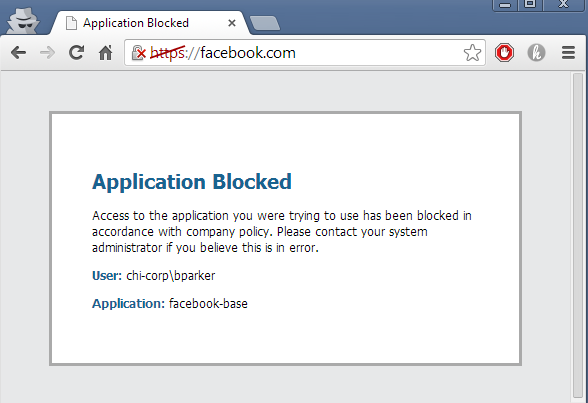
To test URL Filtering again, switch the security rule back to the URL filtering profile used previously and Commit.
In Chrome using https://facebook.com: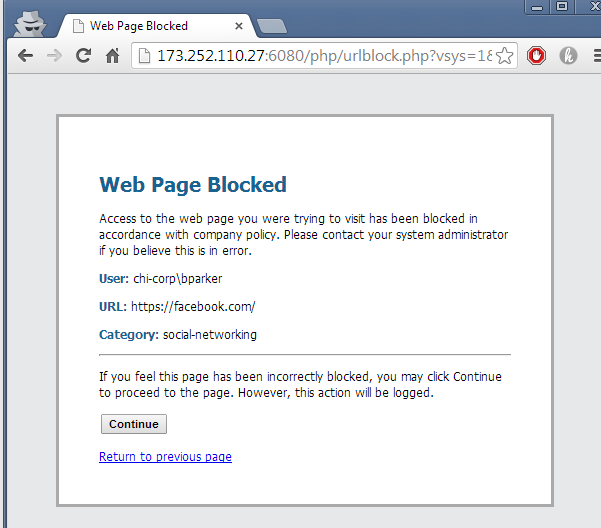

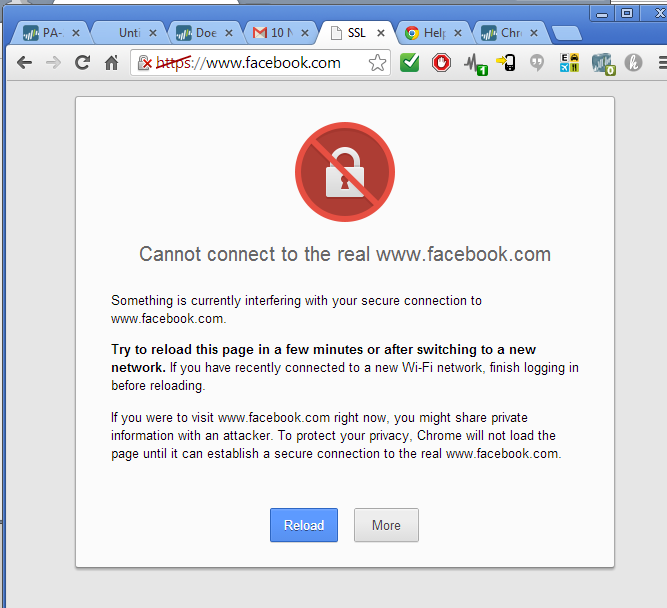
However, please note that before testing an error was received like the one below, so Chrome depending on extensions and other security features, can have more security and can search for invalid SSL credentials to catch "Man in the Middle attacks".
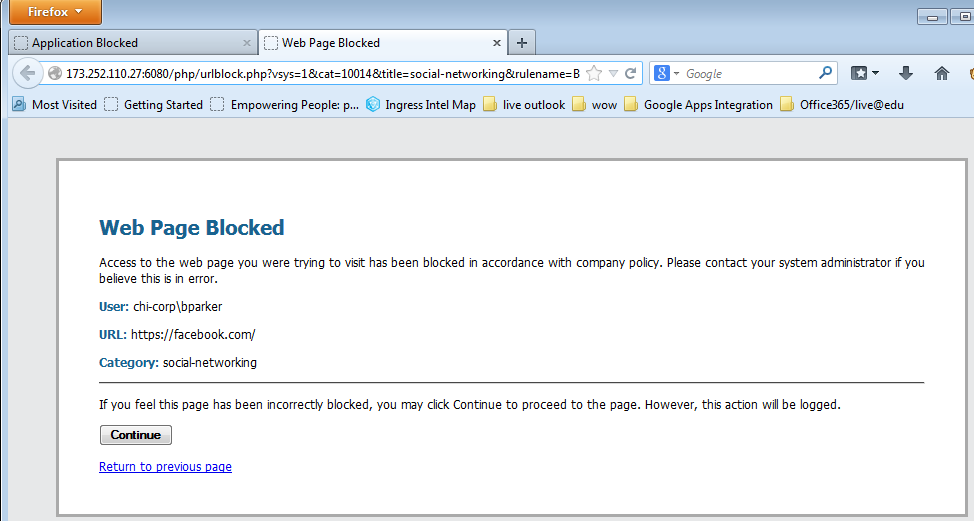
No comments:
Post a Comment