How to Block Internet Explorer (all versions) from Internet Access
Question
In a scenario where a certain web-browser needs to be completely blocked for http or https, Palo Alto NGFW can provide granular control via custom signatures. In our example, it'd be the ubiquitous Internet Explorer. The requirement is to prevent only the http or https traffic, any other protocol using the browser (e.g. ftp) should be allowed. How to achieve this?
Answer
NOTE: Decryption is a must for https traffic. We need to have full visibility on the traffic after the SSL-handshake.
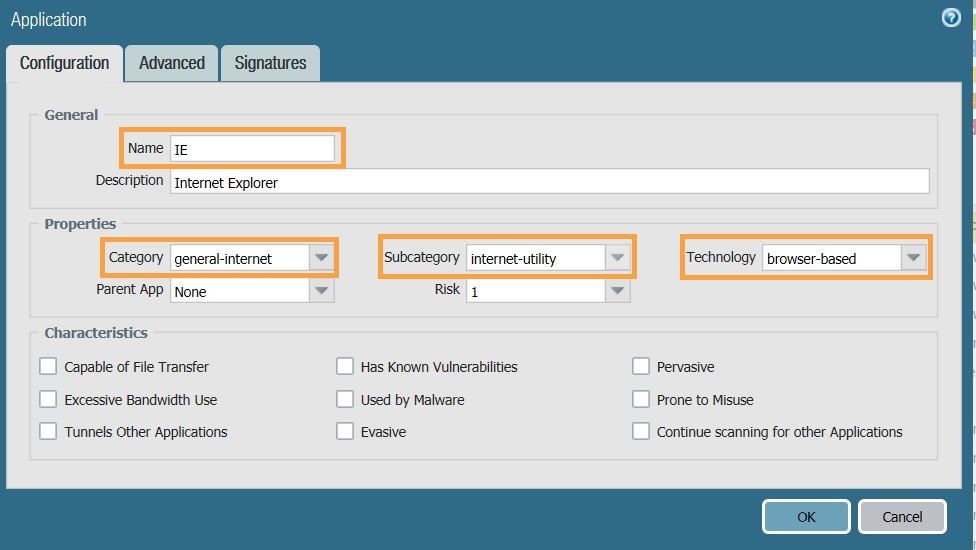
- Navigate to the Objects tab. Under 'Applications', click on the 'Add' option to create a new application.
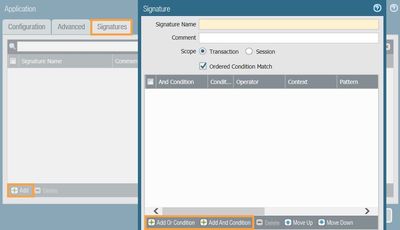
Give a suitable name, category, sub-category and technology. - Under the 'Signatures' tab, click on 'Add' to add a new signature. This will open a pop-up box.
- After providing an appropriate name, click either on 'Add or Condition' or 'Add and Condition'. Since we are adding a single condition, either option is fine. However, If you are adding multiple conditions, please choose the operator suitably.
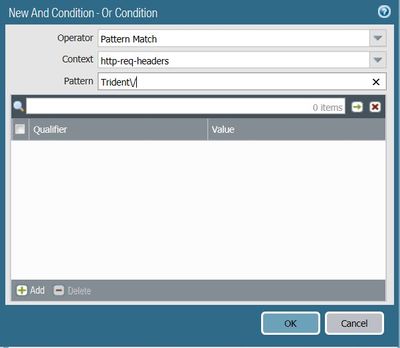
- Choosing the 'Or condition' or 'And condition' option would open another pop-up box. Here, you should choose the following:
- Operator - Pattern Match
- Context - http-req-headers
- Pattern - Trident\/
- Lastly, add it to a particular Deny policy. As a slight difference, you can choose the action as 'Reset (with client, server or both)'. This will end the session faster and free up resources on the firewall quicker.
Verification:
If everything was configured correctly, we should see the proper action taken by the firewall. As a result, the traffic logs should look like this: 

On the client, the browser will immediately show 'This page cannot be displayed' or similar message.
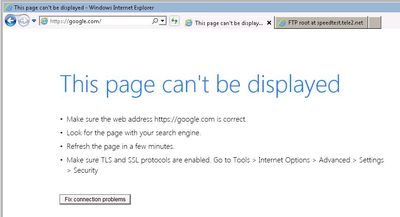
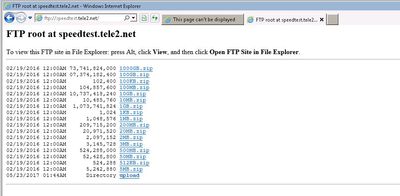
However, as expected FTP access through the web-browser works just fine.
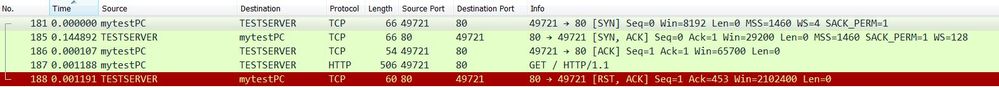
If we take the packet-captures, we'd observe the RST packet injected in the TCP stream:
Additional comments:
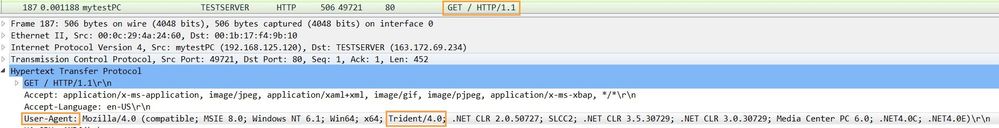
This signature is derived from the 'User-Agent' field in the GET packet. The same technique can be used to match for other web-browsers or different versions, if needed. For example, to match all the versions of firefox, the pattern would be Firefox\/ and so on.
owner - ansharma
____________________________________________________________________________________________________________________
____________________________________________________________________________________________________________________
How to allow/block Dropbox application
- Dropbox has both a web browser interface and a desktop client (a special folder).
- Traffic from both the interfaces is SSL based and is identified as ‘dropbox’ App-ID.
- To identify uploads and downloads:
- Configure a SSL decryption rule for the traffic and inspect the content inside.
- With the browser interface, decrypt the traffic and apply a file blocking profile to block upload, download, or both.
- The desktop client does not accept a MITM certificate and will fail to connect when SSL decryption rules are used.
- Configure a SSL decryption rule for the traffic and inspect the content inside.
- With the browser interface, decrypt the traffic and apply a file blocking profile to block upload, download, or both.
- The desktop client does not accept a MITM certificate and will fail to connect when SSL decryption rules are used.
How to Block Google Chrome
Steps
Note: For this process to work for HTTPS sites, SSL decryption needs to be configured. To configure SSL decryption, see How to Implement SSL Decryption.
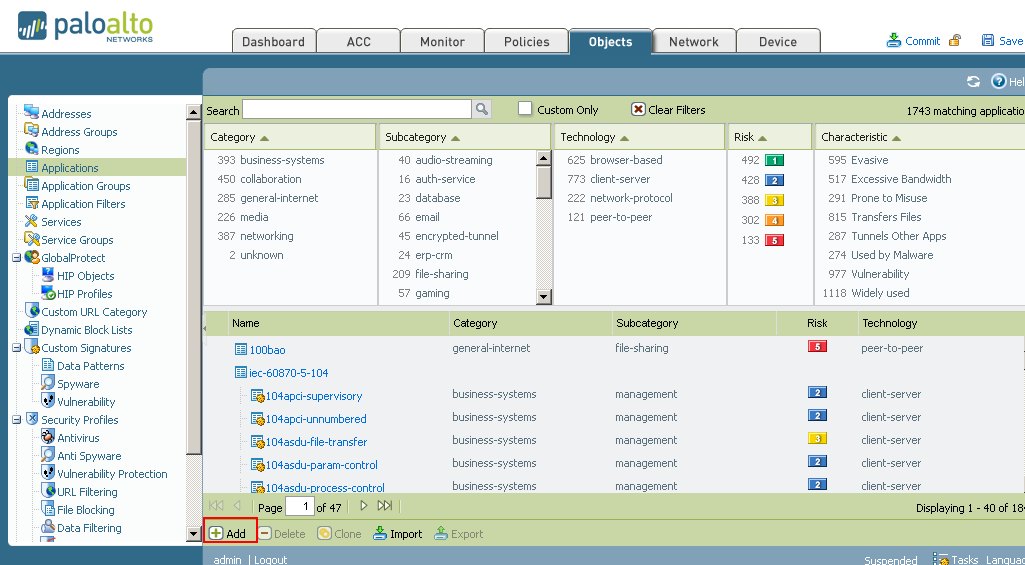
- From the Objects tab, navigate to Applications and select "Add":
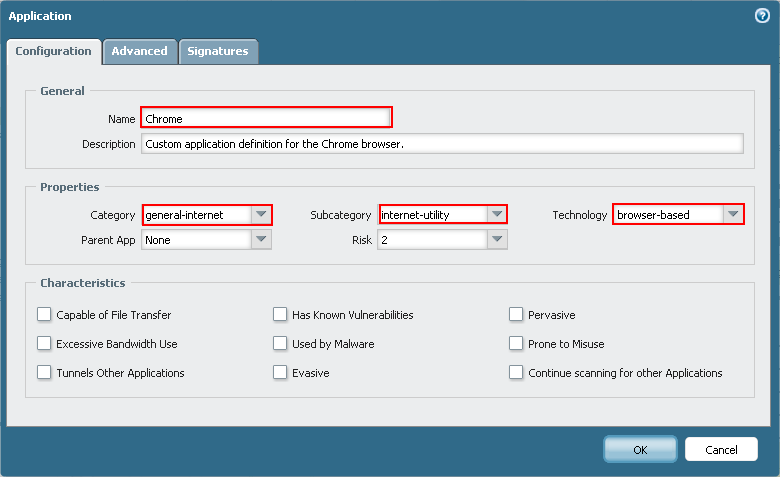
- In the Application window, fill out the required categories. These are: Name, Category, Subcategory, and Technology. Choosing a Parent App and Risk is not required. An example is shown below:
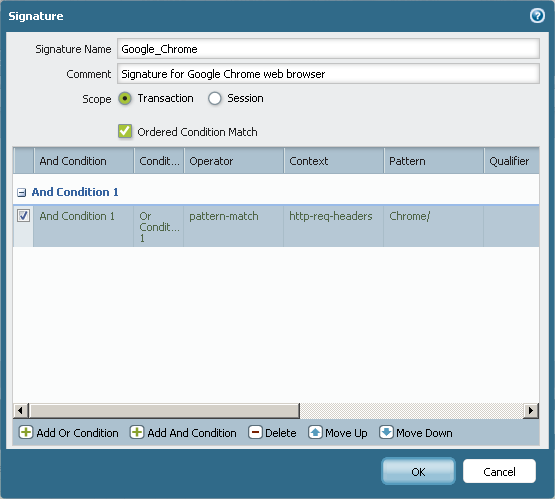
- On the Signature tab, enter a name for the signature and (optionally) a comment for the signature.
- Select "Transaction" for the scope.
- Add an OR condition with the following settings and select OK:
- Operator: Pattern Match
- Context: http-req-headers
- Pattern: Chrome/
- Press OK again and commit your change.
Security policies can now reference the custom application. Once a security policy is added to block the custom application, "Chrome", new sessions will be blocked.
owner: cstancill
Note: For this process to work for HTTPS sites, SSL decryption needs to be configured. To configure SSL decryption, see How to Implement SSL Decryption.
- From the Objects tab, navigate to Applications and select "Add":

- In the Application window, fill out the required categories. These are: Name, Category, Subcategory, and Technology. Choosing a Parent App and Risk is not required. An example is shown below:

- On the Signature tab, enter a name for the signature and (optionally) a comment for the signature.
- Select "Transaction" for the scope.
- Add an OR condition with the following settings and select OK:
- Operator: Pattern Match
- Context: http-req-headers
- Pattern: Chrome/

- Press OK again and commit your change.
Security policies can now reference the custom application. Once a security policy is added to block the custom application, "Chrome", new sessions will be blocked.
owner: cstancill

No comments:
Post a Comment