What is Global Catalog ?
A global catalog is a distributed data storage that is stored in domain controllers (also known as global catalog servers) and is used for faster searching. It provides a searchable catalog of all objects in every domain in a multi-domain Active Directory Domain Services (AD DS). A global catalog provides a partial representation of the objects and is distributed using multi-master replication.
Active Directory Integrated Zones ?
using AD integrated zones you can benefit from:
- Replication of the zones using AD replication
- Securing the zone as you can only only secure updates
- Having more than one primary zone for your domain
Active Directory Integrated Zones
Active Directory integrated zone data is stored as an Active Directory object and is replicated as part of domain replication. This has the following advantages:
- No single point of failure: with Active Directory integrated zones, changes made by using the dynamic update protocol can be made to any server that hosts the Active Directory integrated zone, rather than to a single server.
- Fault tolerance: all Active Directory integrated zones are primary zones. Therefore, each domain controller that hosts an Active Directory integrated zone maintains the zone information. Only domain controllers that reside in the Active Directory domain in which the zone data is stored can host the zone.
- Single replication topology: zone transfers occur automatically as part of Active Directory replication, eliminating the need to configure replication for DNS and Active Directory separately.
- Secure dynamic updates: with Active Directory integrated zones, you can set permissions on zones and records within them. Updates that use the dynamic update protocol can only come from authorised computers. You can only create Active Directory integrated zones on servers that are configured as domain controllers and that have the DNS Server service installed.
Active Directory Replication
Without proper and timely replication, a domain will be unable to function effectively. Replication is the process of sending update information for data that has changed in the directory to other domain controllers. It is important to have a firm understanding of replication and how it takes place, both within the domain and in multiple-site environments.
There are three main elements or components that are replicated between domain controllers: the domain partition replica, the global catalog and the schema.
The domain partition replica is the Active Directory database of a domain. Each domain controller maintains a duplicate copy of its local domain partition replica. Domain controllers do not maintain copies of replicas from other domains. When an administrator makes a change to the domain, that change is replicated to all domain controllers immediately.
Each forest contains only a single global catalog. By default, the first domain controller installed into a forest is the global catalog server. The global catalog contains a partial replica of every object within each domain of the forest. The global catalog serves as a master index for the forest, which allows for easy and efficient searching for users, computers, resources and other objects. Any domain controller can be configured to act as a peer global catalog server. You should have at least two global catalog servers per domain and at least one per site. As changes are made to objects within the forest, the global catalog is updated. Once the global catalog is changed on one domain controller, it is replicated to all other domain controllers in the forest.
Every domain controller in a forest has a copy of the schema. Just as with changes to the Active Directory database (i.e., domain partition replica), any changes to the Active Directory schema are replicated to all other domain controllers in the forest. Fortunately, the schema is usually static so there is little replication traffic caused by schema changes.
distributed file system (DFS)
A distributed file system is a client/server-based application that allows clients to access and process data stored on the server as if it were on their own computer. When a user accesses a file on the server, the server sends the user a copy of the file, which is cached on the user's computer while the data is being processed and is then returned to the server.
A distributed file system (DFS) is a file system with data stored on a server. The data is accessed and processed as if it was stored on the local client machine. The DFS makes it convenient to share information and files among users on a network in a controlled and authorized way. The server allows the client users to share files and store data just like they are storing the information locally. However, the servers have full control over the data and give access control to the clients.
What is SNMP?
Simple Network Management Protocol (SNMP) is an application–layer protocol defined by the Internet Architecture Board (IAB) in RFC1157 for exchanging management information between network devices. It is a part of Transmission Control Protocol⁄Internet Protocol (TCP⁄IP) protocol suite.
SNMP is one of the widely accepted protocols to manage and monitor network elements. Most of the professional–grade network elements come with bundled SNMP agent. These agents have to be enabled and configured to communicate with the network management system (NMS).
What is Certificates ?
A Public Key certificate commonly called Certificate is a digitally signed statement that binds the value of a public key to the identity of the person, device, or service that holds the corresponding private key.
The entity that receives the certificate is the subject of the certificate. The issuer and signer of the certificate is a certification authority.
Why use a digital certificate?
There are two main reasons of using a digital certificate:
1. To prove your company's (or your server's) identity online and in so doing create a sense of trust and confidence in using your web site.
2. To offer protection of the data submitted to your web site (or between servers) through the use of encryption. Should any information be intercepted, it will be unintelligible without the unique key used for decryption.
A Digital Certificate is issued by a Certification Authority (CA) and signed with the CA's private key.
A Digital Certificate typically contains the:
Owner's public key
Owner's name
Expiration date of the public key
Name of the issuer (the CA that issued the Digital Certificate
Serial number of the Digital Certificate
Digital signature of the issuer
Private Key/Public Key
The encryption using a private key/public key pair ensures that the data can be encrypted by one key but can only be decrypted by the other key pair .
The trick in a key pair is to keep one key secret (the private key) and to distribute the other key (the public key) to everybody. Anybody can send you an encrypted message, that only you will be able to decrypt.
Types of digital certs…..
Server Certificates: Enable Web servers to operate in a secure mode. A Server Certificate unambiguously identifies and authenticates your server and encrypts any information passed between the server and a Web browser.
Personal Digital Certificates(User certs): Used by individuals when they exchange messages with other users or online services.
Machine certificates: Used to identify individual devices

1) Explain tcp timers?
a)Retransmission Timer – To retransmit lost segments, TCP uses retransmission timer (RTO). When TCP sends a segment the timer starts and stops when the acknowledgment is received
b)Persistent Timer – To deal with a zero-window-size
c) Keep Alive Timer – A keepalive timer is used to prevent a long idle connection between two TCPs. If a client opens a TCP connection to a server transfers some data and becomes silent the client will crash. In this case, the connection remains open forever. So a keepalive timer is used. Each time server hears from a client, it resets this timer. The time-out is usually 2 hours. If the server does not hear from the client after hours, it sends a probe segment. If there is no response after 10 probes, each of which is 75 s apart, it assumes that the client is down and terminates the connection.
d) Time Wait Timer – This timer is used during tcp connection termination. The timer starts after sending the last Ack for 2nd FIN and closing the connection
What does window size indicate?
The amount of data the receiver can receive at one point of time. For every ACK there will be WS and it can vary.
The amount of data the receiver can receive at one point of time. For every ACK there will be WS and it can vary.
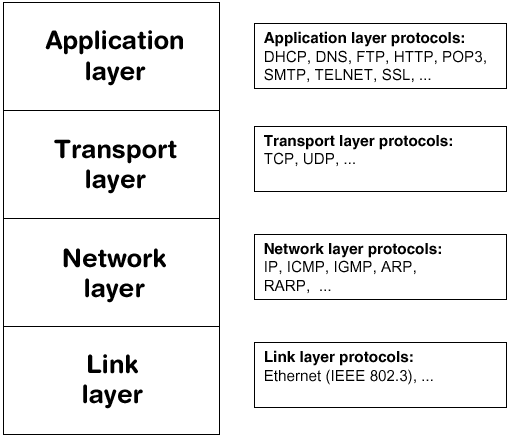
.What are the different protocols works at each of the layers?
Application layer - HTTP, FTP, SMTP, SNMP, DNS, DHCP, TELNET
Presentation layer - TLS (Transport layer security), MIME (Multi-purpose Internet Mail Extension), NCP(Network control program)
Session layer - SSL, SIP, SAP, NetBIOS
Transport layer - TCP, UDP
Network layer - IPv4, IPv6, ICMP, IGMP, IPSEC
Data-Link layer - ATM, Frame relay, PPP
Physical layer - USB, Ethernet
Application layer - HTTP, FTP, SMTP, SNMP, DNS, DHCP, TELNET
Presentation layer - TLS (Transport layer security), MIME (Multi-purpose Internet Mail Extension), NCP(Network control program)
Session layer - SSL, SIP, SAP, NetBIOS
Transport layer - TCP, UDP
Network layer - IPv4, IPv6, ICMP, IGMP, IPSEC
Data-Link layer - ATM, Frame relay, PPP
Physical layer - USB, Ethernet
1) What are the functions of Transport, Network and Datalink layers?
Data link layer(L2) deals with Switch. Mac address and also error checksum using LLC(logical link control) to ensure all frames are transfered to the next layer.
Data link layer is the 2nd layer of the OSI model. Switches operates at this layer. Data is in the form of frames. Each frames has a header and trailer. The header portion contains the source and destination mac address. The trailer portion contains the frame check sequence used for error detection. It is of two types,
a) LLC deals with error detection and flow control.
b) Mac defines hardware addressing.
Network layer is the 3rd layer of the OSI model.Routers operates at this layer. Routers provide logical addressing (IP) for path determination. Data is in the form of packets. IP address is used to identify a host on a network.
Data link layer(L2) deals with Switch. Mac address and also error checksum using LLC(logical link control) to ensure all frames are transfered to the next layer.
Data link layer is the 2nd layer of the OSI model. Switches operates at this layer. Data is in the form of frames. Each frames has a header and trailer. The header portion contains the source and destination mac address. The trailer portion contains the frame check sequence used for error detection. It is of two types,
a) LLC deals with error detection and flow control.
b) Mac defines hardware addressing.
Network layer is the 3rd layer of the OSI model.Routers operates at this layer. Routers provide logical addressing (IP) for path determination. Data is in the form of packets. IP address is used to identify a host on a network.
What is fragmentation and explain how IP will handle the fragmentation.
If the size of the IP packet is more than the MTU size and is the DF is not set to 1 frag is needed. IP frag breaks packets into smaller pieces and sends to the destination. Frag reassembly happens at two instances, 1. Destination host. 2. If the firewall is inbetween the client and server, it does a DPI to check the type of the data being forwarded.
4) Define Unicast, Multicast and Broadcast. What is the use of Multicast?
Unicast - It is sent to a specific devices and not to a group of devices on a lan.
Multicast - It it one to many or many to many distribution. Point to multipoint communication. It is used for replicating the packet to reach multiple receivers when necessary.
Broadcast - It is delivered to all devices on a LAN.
5) What are the different Classes of IP address and give the range of each class
Class A - 0 - 126
Class B - 128 - 191
Class C - 192 - 223
Class D - 224 - 239
Class E - 240 - 255
6) What is network id , broadcast id and subnet mask?
Network ID - Used to identify a L3 device on a network.
Broadcast ID - It is the last address of a network.
Subnet Mask - It defines the range of IP address that can be used in a network.
7) What is the subnetwork address if the destination address is 200.45.34.56 and the subnet mask is 255.255.240.0?
200.45.34.56 - 255.255.240.0
Subnetwork address : 200.45.0.0/20
8) ARP works at which layer and Why?
ARP works in L2. The reason is, ARP is encapsulated in the E2 frame to resolve the Mac address with the help of IP address.
9) Which ICMP message confirms the traceroute is completed?
ICMP echo reply - Type 0 code 0 confirms the traceroute is completed - Windows.
UDP - Destination unreachable Port unreachable - Type 3 Code 3 - Linux
10) What is the importance of DF, MF flag, offset ?
DF is dont fragment - Determines whether the frag is required. If DF = 1, Frag doesn't occur.
MF is More Frag - Determines more packets are yet to receive by the destination, If MF = 1.
Offset - The field indicates where in the datagram this frag belongs.
11) What does the protocol field determines in the IP packet?
Protocol - It informs to which protocol stack the datagram has to be deliverd. Determined by a protocol number.
12) Explain 3 way handshake process?
A three-way handshake is a method used in a TCP/IP network to create a connection between a local host/client and server. It is a three-step method that requires both the client and server to exchange SYN and ACK packets before actual data communication begins.
13) What does window size indicate?
The amount of data the receiver can receive at one point of time. For every ACK there will be WS and it can vary.
14) What is the difference between PUSH and URG flag?
PUSH flag is used to push the last small byte that is kept in the buffer. It does not allow the segment to wait in the buffer for a long time.
URG - If the sender wants to send an urgent data, he will look for the current segment and add the urgent flag at the front followed by the normal data. The urgent pointer denotes the end of urgent data.
The receiver receives the segment, identifies the urgent flag and and immediately process the urgent data and sends to the application layer in an out of order fashion.
15) What is the purpose of RST bit?
In RFC, there are three main instances where reset is used.
a) TCP syn request for the port which is not supported.
b) TCP segment which is not the first packet.
c) Sequence and Ack mismatch.
D) When the Keep-Aliver timer expires, the server would reset the connection.
16) Who is responsible for the reliability of UDP packet.
UDP is not a relaible protocol. If relaiblity is required, the sender can use his own mechanism in the application layer. EG) TFTP (Trivial FTP)
17) Why Firewall reassembles the packet?
If the firewall is inbetween the client and server, it does a DPI to check the type of the data being forwarded.
18) What is the difference between Active and Passive FTP?
Active FTP - Initial connection is established by client and Data connection is established by the server. When both client and server are in the same LAN.
Passive FTP- Both initial connection and Data connection is established by the client. When the client is in LAN and the server is in WAN.
19) What is the important of port command?
Port command is used for data transfer. In active FTP, client initiated port command; whereas, in passive FTP, the server initiates the port command.
20) You are not able to access yahoo.com on your private computer, in your home. Please list the steps you will take to find (not necessarily fix) the cause of the problem
1. What is the error you see when you try to access the yahoo.com
2. Are you not able to access only yahoo.com or other websites.
3. If only yahoo, check with different browser.
4. If browser is good, clear the browser cache and cookies.
5. Reset the browser.
6. In command prompt, type 'ping yahoo.com', press Enter & post back the result of the ping test.
7. In command prompt, type 'tracert yahoo.com', press Enter & post back the result of the traceroute test. This is to confirm if the packet is dropped before reaching the destination.
If the size of the IP packet is more than the MTU size and is the DF is not set to 1 frag is needed. IP frag breaks packets into smaller pieces and sends to the destination. Frag reassembly happens at two instances, 1. Destination host. 2. If the firewall is inbetween the client and server, it does a DPI to check the type of the data being forwarded.
4) Define Unicast, Multicast and Broadcast. What is the use of Multicast?
Unicast - It is sent to a specific devices and not to a group of devices on a lan.
Multicast - It it one to many or many to many distribution. Point to multipoint communication. It is used for replicating the packet to reach multiple receivers when necessary.
Broadcast - It is delivered to all devices on a LAN.
5) What are the different Classes of IP address and give the range of each class
Class A - 0 - 126
Class B - 128 - 191
Class C - 192 - 223
Class D - 224 - 239
Class E - 240 - 255
6) What is network id , broadcast id and subnet mask?
Network ID - Used to identify a L3 device on a network.
Broadcast ID - It is the last address of a network.
Subnet Mask - It defines the range of IP address that can be used in a network.
7) What is the subnetwork address if the destination address is 200.45.34.56 and the subnet mask is 255.255.240.0?
200.45.34.56 - 255.255.240.0
Subnetwork address : 200.45.0.0/20
8) ARP works at which layer and Why?
ARP works in L2. The reason is, ARP is encapsulated in the E2 frame to resolve the Mac address with the help of IP address.
9) Which ICMP message confirms the traceroute is completed?
ICMP echo reply - Type 0 code 0 confirms the traceroute is completed - Windows.
UDP - Destination unreachable Port unreachable - Type 3 Code 3 - Linux
10) What is the importance of DF, MF flag, offset ?
DF is dont fragment - Determines whether the frag is required. If DF = 1, Frag doesn't occur.
MF is More Frag - Determines more packets are yet to receive by the destination, If MF = 1.
Offset - The field indicates where in the datagram this frag belongs.
11) What does the protocol field determines in the IP packet?
Protocol - It informs to which protocol stack the datagram has to be deliverd. Determined by a protocol number.
12) Explain 3 way handshake process?
A three-way handshake is a method used in a TCP/IP network to create a connection between a local host/client and server. It is a three-step method that requires both the client and server to exchange SYN and ACK packets before actual data communication begins.
13) What does window size indicate?
The amount of data the receiver can receive at one point of time. For every ACK there will be WS and it can vary.
14) What is the difference between PUSH and URG flag?
PUSH flag is used to push the last small byte that is kept in the buffer. It does not allow the segment to wait in the buffer for a long time.
URG - If the sender wants to send an urgent data, he will look for the current segment and add the urgent flag at the front followed by the normal data. The urgent pointer denotes the end of urgent data.
The receiver receives the segment, identifies the urgent flag and and immediately process the urgent data and sends to the application layer in an out of order fashion.
15) What is the purpose of RST bit?
In RFC, there are three main instances where reset is used.
a) TCP syn request for the port which is not supported.
b) TCP segment which is not the first packet.
c) Sequence and Ack mismatch.
D) When the Keep-Aliver timer expires, the server would reset the connection.
16) Who is responsible for the reliability of UDP packet.
UDP is not a relaible protocol. If relaiblity is required, the sender can use his own mechanism in the application layer. EG) TFTP (Trivial FTP)
17) Why Firewall reassembles the packet?
If the firewall is inbetween the client and server, it does a DPI to check the type of the data being forwarded.
18) What is the difference between Active and Passive FTP?
Active FTP - Initial connection is established by client and Data connection is established by the server. When both client and server are in the same LAN.
Passive FTP- Both initial connection and Data connection is established by the client. When the client is in LAN and the server is in WAN.
19) What is the important of port command?
Port command is used for data transfer. In active FTP, client initiated port command; whereas, in passive FTP, the server initiates the port command.
20) You are not able to access yahoo.com on your private computer, in your home. Please list the steps you will take to find (not necessarily fix) the cause of the problem
1. What is the error you see when you try to access the yahoo.com
2. Are you not able to access only yahoo.com or other websites.
3. If only yahoo, check with different browser.
4. If browser is good, clear the browser cache and cookies.
5. Reset the browser.
6. In command prompt, type 'ping yahoo.com', press Enter & post back the result of the ping test.
7. In command prompt, type 'tracert yahoo.com', press Enter & post back the result of the traceroute test. This is to confirm if the packet is dropped before reaching the destination.
Second Set of Answers:
1) How traceroute works?
Traceroute is the comand used in linux OS to find the path from the source to destination. To identify if the packet has reached the destination it give a message
Destination Unreachable(Port unreachable)
2) What is the difference between traceroute and tracert?
Traceroute is used to determine the path the packet has travelled from source to detiantion in Linux OS it give a message Destination Unreachable (Port unreachable)(Type3 code 3)
Tracert is used to determine the path the packet has travelled from source to detiantion in a windows OS it give a Echo reply.(Type0 Code 0)
3) Why there are three columns in traceroute results?
Traceroute has three coloumns
a)First Coloumn indicates the Hop count
b)Time taken to reach the destination
c)IP address of each hop.
4) What does * indicate in traceroute result?
*indicats the ping request is reached but does not provide the reply of that particular hop IP address due to some security features enabled.
5) What is the purpose of relay agent?
Relay Agent is Configured in routers when the DHCP server is another network.
6) Is DHCP decline message is sent by Client or Server? Explain
DHCP decline message is sent by the client. The client performs this procedure by sending (ARP) requests for the IP address provided in the DHCP ACK. If the client detects that the address is already in use by receiving a reply to the ARP request, the client will send a DHCP DECLINE message to the server and restarts the configuration process again.
7) Explain zone transfer?
Zone Transfer is used to update the records in secondary server.Any changes made in the primary server will update in the secondary server.There are two types of zone transfer
a)AXFR(All file zone tranfer)
b)IXFR(incremental file zone transfer)
8) What are the types of records?
The different types of records are A ,AAAA, SOA,PTR,CNAME,MX
9) When will DNS use TCP?
When DNS zone transfer happens and the file size is large that is greater than 512 Bytes it uses TCP.
10) Explain DNS query process.
a). When we open web browser and enter www.google.com in the address field. At that point, the computer doesn't know the IP address for www.google.com, so it sends a DNS query to the ISP's DNS server (The DNS server address is obtained by the use of DHCP).
b). The ISP's DNS server doesn't know the IP address for www.google.com, so it will ask one of the ROOT DNS servers.
c). The ROOT DNS server checks its database and finds no entry for google.com, but, it does know where to forward the local DNS server.
d). The local DNS sever now contacts the TLD which is TOP Level Domain. The TLD has the domain names of top level domains such as .com, .org, .net and so on. The TLD still doesn't know the IP address of google.com. Hence, it forwards the DNS query to the next and final level.
e). The local DNS server now contacts the Authorative Name server which knows everything about the domain name which includes the IP address. The ANS now directs to the google's DNS server to get the IP address of google.com.
f). Google's DNS server checks its database and finds an entry for www.google.com. This entry has an IP address of 8.8.8.8. Since the IP address of the DNS server and webserver (www) are identical, this means they are likely to be both on the same physical server.
g). Your ISP's DNS server now knows the IP address for www.google.com and sends the result to our computer.
h). Our computer now knows the IP address of google's website and is able to directly contact it. Naturally, the next step is to send an http request directly to google's webserver and download the webpage.
11) Explain Iterative & recursive query
Iterative Query :Iterative DNS queries are in which a DNS server is queried and returns an answer without querying other DNS servers, even if it cannot provide a definitive answer.Server Uses both iterative and recursive query
Recursive Query:Recursive DNS queries occur when a DNS client requests information from a DNS server that is set to query another DNS servers until a definitive answer is returned to the client. The queries made to subsequent DNS servers from the first DNS server are iterative queries.PC always uses Recursive Query.
12) What is MDI & MDIX ports?
MDI/MDIX is a type of Ethernet port connection using twisted pair cabling. The MDI (medium dependent interface) is the component of the media attachment unit (MAU) that provides the physical and electrical connection to the cabling medium. An MDIX (MDI crossover) is a version of MDI that enables connection between like devices. MDI ports connect to MDIX ports via straight-through twisted pair cabling; both MDI-to-MDI and MDIX-to-MDIX connections use crossover twisted pair cabling.
13) Explain Straight Through & Cross Over cabling. Where will it be used.
1)Straight through cable to connect different type of devices.
a) Connect a computer to a switch
b) Connect a computer to a cable modem's LAN port.
c) Connect a router's LAN port to a switch for expanding network)
d) Connect 2 switches
2) A crossover cable can be used to:
a) Connect 2 computers directly.
2) Connect a router's LAN port to a switch used for expanding network
3) Connect 2 switches normal port in both switches.
14) What is Proxy ARP and in which scenario you will enable proxy ARP.
Proxy Arp is enabled only when the PC do an AND opearation to find the Mac address of the destination host and it feels it is in the same network, but physically it is connected in the another network the proxy ARP is enabled in the router to pass the packet.
15) Explain SACK?
SACK is selective acknoledgement , used in TCP to resend only the lost segement. SACK should be permited by both sender and receiver during the three way handshake else both cant use SACK, it avoid duplicate segments.
16. Client has MTU of 1200 and Receiver has MTU of 1400, what value of MTU will be used by Client?
Client uses an MTU of 1200.
17) in 8 DHCP messages how many Are broadcast?
Discover, Offer, Request, Acknowledgement messages are broadcast.
18) what is DHCP release?
DHCP release:
Once the DHCP IP lease time is finished, the IP will be released from the PC and it perform DORA process to acquire new IP.
19) what is the use of WSF and what if wsf,Sack is not shared during tcp handshake
WSF-Windows Scaling Factor is an option to increase the receive window size if the data sent is greater that the maximum value 65,535 bytes.WSF is negotiated only once when an TCP connection is established.
20) Explain PMTUD and what are the Error code
- PMTUD-Path Maximum Transfer Unit Discovery
- usually with the goal of avoiding IP fragmentation
It sends sample data of 1 byte and checks the MTU along the path and PC fragements with lowest MTU. Error message used in PMTUD is Type:3, code 0.
1) How traceroute works?
Traceroute is the comand used in linux OS to find the path from the source to destination. To identify if the packet has reached the destination it give a message
Destination Unreachable(Port unreachable)
2) What is the difference between traceroute and tracert?
Traceroute is used to determine the path the packet has travelled from source to detiantion in Linux OS it give a message Destination Unreachable (Port unreachable)(Type3 code 3)
Tracert is used to determine the path the packet has travelled from source to detiantion in a windows OS it give a Echo reply.(Type0 Code 0)
3) Why there are three columns in traceroute results?
Traceroute has three coloumns
a)First Coloumn indicates the Hop count
b)Time taken to reach the destination
c)IP address of each hop.
4) What does * indicate in traceroute result?
*indicats the ping request is reached but does not provide the reply of that particular hop IP address due to some security features enabled.
5) What is the purpose of relay agent?
Relay Agent is Configured in routers when the DHCP server is another network.
6) Is DHCP decline message is sent by Client or Server? Explain
DHCP decline message is sent by the client. The client performs this procedure by sending (ARP) requests for the IP address provided in the DHCP ACK. If the client detects that the address is already in use by receiving a reply to the ARP request, the client will send a DHCP DECLINE message to the server and restarts the configuration process again.
7) Explain zone transfer?
Zone Transfer is used to update the records in secondary server.Any changes made in the primary server will update in the secondary server.There are two types of zone transfer
a)AXFR(All file zone tranfer)
b)IXFR(incremental file zone transfer)
8) What are the types of records?
The different types of records are A ,AAAA, SOA,PTR,CNAME,MX
9) When will DNS use TCP?
When DNS zone transfer happens and the file size is large that is greater than 512 Bytes it uses TCP.
10) Explain DNS query process.
a). When we open web browser and enter www.google.com in the address field. At that point, the computer doesn't know the IP address for www.google.com, so it sends a DNS query to the ISP's DNS server (The DNS server address is obtained by the use of DHCP).
b). The ISP's DNS server doesn't know the IP address for www.google.com, so it will ask one of the ROOT DNS servers.
c). The ROOT DNS server checks its database and finds no entry for google.com, but, it does know where to forward the local DNS server.
d). The local DNS sever now contacts the TLD which is TOP Level Domain. The TLD has the domain names of top level domains such as .com, .org, .net and so on. The TLD still doesn't know the IP address of google.com. Hence, it forwards the DNS query to the next and final level.
e). The local DNS server now contacts the Authorative Name server which knows everything about the domain name which includes the IP address. The ANS now directs to the google's DNS server to get the IP address of google.com.
f). Google's DNS server checks its database and finds an entry for www.google.com. This entry has an IP address of 8.8.8.8. Since the IP address of the DNS server and webserver (www) are identical, this means they are likely to be both on the same physical server.
g). Your ISP's DNS server now knows the IP address for www.google.com and sends the result to our computer.
h). Our computer now knows the IP address of google's website and is able to directly contact it. Naturally, the next step is to send an http request directly to google's webserver and download the webpage.
11) Explain Iterative & recursive query
Iterative Query :Iterative DNS queries are in which a DNS server is queried and returns an answer without querying other DNS servers, even if it cannot provide a definitive answer.Server Uses both iterative and recursive query
Recursive Query:Recursive DNS queries occur when a DNS client requests information from a DNS server that is set to query another DNS servers until a definitive answer is returned to the client. The queries made to subsequent DNS servers from the first DNS server are iterative queries.PC always uses Recursive Query.
12) What is MDI & MDIX ports?
MDI/MDIX is a type of Ethernet port connection using twisted pair cabling. The MDI (medium dependent interface) is the component of the media attachment unit (MAU) that provides the physical and electrical connection to the cabling medium. An MDIX (MDI crossover) is a version of MDI that enables connection between like devices. MDI ports connect to MDIX ports via straight-through twisted pair cabling; both MDI-to-MDI and MDIX-to-MDIX connections use crossover twisted pair cabling.
13) Explain Straight Through & Cross Over cabling. Where will it be used.
1)Straight through cable to connect different type of devices.
a) Connect a computer to a switch
b) Connect a computer to a cable modem's LAN port.
c) Connect a router's LAN port to a switch for expanding network)
d) Connect 2 switches
2) A crossover cable can be used to:
a) Connect 2 computers directly.
2) Connect a router's LAN port to a switch used for expanding network
3) Connect 2 switches normal port in both switches.
14) What is Proxy ARP and in which scenario you will enable proxy ARP.
Proxy Arp is enabled only when the PC do an AND opearation to find the Mac address of the destination host and it feels it is in the same network, but physically it is connected in the another network the proxy ARP is enabled in the router to pass the packet.
15) Explain SACK?
SACK is selective acknoledgement , used in TCP to resend only the lost segement. SACK should be permited by both sender and receiver during the three way handshake else both cant use SACK, it avoid duplicate segments.
16. Client has MTU of 1200 and Receiver has MTU of 1400, what value of MTU will be used by Client?
Client uses an MTU of 1200.
17) in 8 DHCP messages how many Are broadcast?
Discover, Offer, Request, Acknowledgement messages are broadcast.
18) what is DHCP release?
DHCP release:
Once the DHCP IP lease time is finished, the IP will be released from the PC and it perform DORA process to acquire new IP.
19) what is the use of WSF and what if wsf,Sack is not shared during tcp handshake
WSF-Windows Scaling Factor is an option to increase the receive window size if the data sent is greater that the maximum value 65,535 bytes.WSF is negotiated only once when an TCP connection is established.
20) Explain PMTUD and what are the Error code
- PMTUD-Path Maximum Transfer Unit Discovery
- usually with the goal of avoiding IP fragmentation
It sends sample data of 1 byte and checks the MTU along the path and PC fragements with lowest MTU. Error message used in PMTUD is Type:3, code 0.
1) Explain tcp timers?
a)Retransmission Timer – To retransmit lost segments, TCP uses retransmission timer (RTO). When TCP sends a segment the timer starts and stops when the acknowledgment is received
b)Persistent Timer – To deal with a zero-window-size
c) Keep Alive Timer – A keepalive timer is used to prevent a long idle connection between two TCPs. If a client opens a TCP connection to a server transfers some data and becomes silent the client will crash. In this case, the connection remains open forever. So a keepalive timer is used. Each time server hears from a client, it resets this timer. The time-out is usually 2 hours. If the server does not hear from the client after hours, it sends a probe segment. If there is no response after 10 probes, each of which is 75 s apart, it assumes that the client is down and terminates the connection.
d) Time Wait Timer – This timer is used during tcp connection termination. The timer starts after sending the last Ack for 2nd FIN and closing the connection.
2) How far we can extend WSF value?
Maximum value is 2^14 (16,384 bytes).
3) In which case dhcp server will unicast.
When the DHCP server in is another network Relay agent is configured in the router and the packet is unicasted from the router to the DHCP server.
4) Why we have time wait state in 4 way handshake.
Time Wait is to make sure that the final ACK is not lost.IT used the 2MSL(Maximum Segment Life) it is the Time it takes and the connection is closed once the time expires.
5) How to differentiate fragmented and non-fragmented packets?
Based on the MF flag, offset value and the Identifier.
6) ping from 192.168.2.10/16 to 192.168.1.10/24
in a same switch? no routers connected. what will be the result?
a)Intially it performs AND operation with /16 and finds that they are in the same network.
b)Sends an ARP request to get the MAc address of the destination.
c)Once an ARP request is resolved it sends an ICMP Request message to the ip 192.168.1.10/24
d)Destiantion perform an AND operation with /24 and find they are in different network
e)ICMP reply will be sent with an error message "Request Timed Out".
7. Differecne between urg and push ?
Urgent flag is raised to prioratise data, from the sender side urgent data starting byte is denoted by urgent flag and end byte is denoted by urgent pointer, followed by the normal data. From the receiver end it extracts the urgent data between urgent flag and urgent pointer and forward to application layer in out of fashion order .
Push flag is raised by sender to avoid segment not to wait in buffer and push the data to receiver and it does not change the sequence order .
8) What is inter vlan routing?
Inter vlan is used to communicate with different vlan. It can be enabled in L3 switch (SVI) and router .
In L3 Switch it is done using TAG port ( to communicate with different VLAN in case of same subnet) and ACCESS port ( no communicate with multi vlan)
9) What is a broadcast domain and a collision domain?
A collision domain:
It is an area in a network where two ethernet frames can collide on one link between two devices. If one emits and if the other emits data at the same time, it creates the collision.
Broadcast domain:
ethernet frames to a mac address destination: FF:FF:FF:FF:FF:FF, it means that it is for all devices that are directly connected to the emitting device. FF:FF:FF:FF:FF:FF is called the broadcast mac address. All the devices who receive it are connected by a SWITCH or switches.
10) What is a VLAN and how it will reduce the broadcast traffic?
VLANs can help manage broadcast traffic by forming multiple broadcast domains. Breaking up a large network into smaller independent segments reduces the amount of broadcast traffic each network device and network segment has to bear.
11) What is a native VLAN what type of traffic will go through native VLAN
In every L3 switch there is one native VLAN ,and it can be changed but has to make sure in all other device Native vlan is changed . As in all device the Native VALN is same when is packet is received with no VLAN tag it is moved to Native VLAN in that switch.
12. What are the different port states and timers and BPDU
1.a Five port states.
a) Blocking
b) Listening
c) Learning
d) Forwarding
e) Disabled
1.b. There are three kinds of BPDUs
a) Configuration BPDU, used by Spanning tree protocol to provide information to all switches.
b) TCN (Topology Change Notification), tells about changes in the topology.
c) TCA (Topology Change Acknowledgment), confirms the reception of the TCN.
13. STP convergence with 4 switches, what is the Root port election criteria
If a Switch has multiple paths to reach the Root Bridge (Root Switch), it must select one path and the associated port as the Root Port. Following are the different steps for selecting the Root Bridge (Switch).
Spanning Tree Root Port selection process in a Non-Root Switch involves the following steps.
a) Select the port connected to the path with the lowest accumulated Spanning Tree Path Cost to the Root Bridge (Root Switch) as the Root Port, when a Non-Root Switch has multiple paths to reach the Root Switch.
b) If multiple paths are available to reach the Root Bridge (Root Switch) with the same accumulated Spanning Tree Path Cost in a Non-Root Switch, select the port connected to the neighbor switch which has the lowest Switch ID value as the Root Port.
c) If all the multiple paths go through the same neighboring switch to reach the Root Bridge (Root Switch), Non-Root Switch will select the local port which receives the lowest port Spanning Tree Port Priority value from neighbor Switch as the Root Port.
d) If the received Spanning Tree Port Priority value values are the same between the connecting ports to reach the Root Bridge (Root Switch), Non-Root Switch will select the port which receives the lowest physical port number from neighbor Switch as the Root Port. This is the last tie breaker.
14. What are the changes a frame undergoes in a switch
In general, layer-2 switching does not modify the frames. A VLAN tag may be added or removed as necessary for frames between tagged and untagged ports. A layer-3 switch is both a router (l3) and switch (l2). When it switches traffic, it's just like any other layer-2 switch.
15. What is a routing table?
A routing table is a set of rules, often viewed in table format, that is used to determine where data packets traveling over an Internet Protocol (IP) network will be directed. All IP-enabled devices, including routers and switches, use routing tables. The basic routing table consists of,
a) Destination.
b) Next hop.
c) Interface.
16. Static routing is when you statically configure a router to send traffic for particular destinations in preconfigured directions.
Dynamic routing is when you use a routing protocol such as OSPF, ISIS, EIGRP, and/or BGP to figure out what paths traffic should take.
16) Define static routing & dynamic routing?
static routing:
Static routing is a form of routing that occurs when a router uses a manually-configured routing entry, rather than information from a dynamic routing traffic.
Dynamic routing:
Dynamic routing is a process where a router can forward data via a different route or given destination based on the current conditions of the communication circuits within a system.
17) What is a default route?
In computer networking, the default route is a setting on a computer that defines the packet forwarding rule to use when no specific route can be determined for a given Internet Protocol destination address.
18) What is a route metric?
Router metrics are metrics used by a router to make routing decisions. A metric is typically one of many fields in a routing table. Metrics are used to determine whether one route should be chosen over another.
19) What is the difference between routing and routed protocol? Give examples.
Routing protocol:
A routing protocol specifies how routers communicate with each other, distributing information that enables them to select routes between any two nodes on a computer network. Routing algorithms determine the specific choice of route.
Eg: OSPF, EIGRP, RIP, RIPV2.
Routed protocol:
A routed protocol is a protocol by which data can be routed. Routed protocol are IP, AppleTalk, and IPX. In this kind of protocols we require an addressing scheme and subnetting.
2) Explain in detail, PC1 wants to communicate to PC2
PCA- 10.0.0.1/24
PCB- 20.0.0.1/24
PCA Perform AND operation to PCB and finds it is in the different network, so it look for the gateway to reach the destination. Once the ARP is resolved, both PC will ping each other.
7) All ports are access ports and no trunk configured on any ports
Will C1 be able to ping C2- No (Both vlan 10 and 20 in the same switch). If we connect vlan 10 access port in vlan 20, it will communicate.
Will C1 be able to ping C3- Yes
Will C1 be able to ping C4- Yes
8) C1 is not able to Ping C3, explain in detail What needs to be done in order to ping between all Machines
- Asked what is the native vlan in both switches (vlan 10 or vlan 20)
- Have enabled trunking in these switches.
- If they need to communicate between all vlan need inter vlan routing.
10) Troubleshoot the scenario where ping from 192.168.0.2 is not working to 20.20.20.2.
192.168.0.2/24----SW----ROUTER----------ROUTER------SW-----20.20.20.0/24
- Asked whether the static routing is enabled or dynamic routing is enabled.
- What is the error message that they received when ping from the source.
- Asked whether the destination host is active.
- Asked to perform traceroute to the destination to check where the packet is dropped.
? What is renewal & rebidding time in DHCP?
In DHCP the default lease time for the IP is 8 days.
Renewal- Once it completed 50%, it send a request message to the server to get the same IP. If there is no reply from the server, the PC, still use the same ip until the lease time expires.
Rebinding- Once it come to 87.5%, client agan send a request to the server to refresh the shcp table to use the same IP.
If the server still not respond and lease time expires, it again do a DORA process to get a new IP.
? If a router is getting a broadcast message, what will it do?
It check the the destination IP address and check their own routing table and forward the packet to the nest hop.
? A switch with 10 ports and 2Lan has been assigned with 5 ports each. How many broadcast domain and collision domain?
Broadcase domain- 1
Collision domain- 10
? Can we connect Trunk link to server PC?
No- Trunk link is used to connect two switches and exchange the same vlan information.
? After control connection, in data connection packets are getting dropped continuously. What are all the possible issue?
- FTP server in the WAN and behind the firewall is blocking.
- Maybe the Natting is not happening.
? In TCP connection establishment, SYN is sent and Rest is received. Why?
- Duce to port number is not supported.
EG: Ftp request send to the HTTP server, server do reset.
1) Explain in detail, PC1 wants to communicate to PC2
PC A :1.1.1.1
PC B :1.1.1.100
When we ping PC 1 to PC 2 it need to do an AND operation as there is not subnet mask present it will not be able to ping from Source to destination.
2)Explain in detail, PC1 wants to communicate to PC2
PCA- 10.0.0.1/24
PCB- 20.0.0.1/24
PCA Perform AND operation to PCB and finds it is in the different network, so it look for the gateway to reach the destination. Once the ARP is resolved, both PC will ping each other.
3) When PC With IP address 1.1.1.1 tries to ping 1.1.1.100 as there are two links present in between the Switch, when the data is sent from A it is sent to switch 1 and it floods the data and B will receive the data twice which forms a loop to avoid these loops we use the concept of STP and block one port with the help of MAC address and path cost.
7) All ports are access ports and no trunk configured on any ports
Will C1 be able to ping C2- No (Both vlan 10 and 20 in the same switch). If we connect vlan 10 access port in vlan 20, it will communicate.
Will C1 be able to ping C3- Yes
Will C1 be able to ping C4- Yes
8) C1 is not able to Ping C3, explain in detail What needs to be done in order to ping between all Machines
- Asked what is the native vlan in both switches (vlan 10 or vlan 20)
- Have enabled trunking in these switches.
- If they need to communicate between all vlan need inter vlan routing.
9) Troubleshoot the scenario where ping from 192.168.0.2 is not working to 20.20.20.2.
192.168.0.2/24----SW----ROUTER----------ROUTER------SW-----20.20.20.0/24
- Asked whether the static routing is enabled or dynamic routing is enabled.
- What is the error message that they received when ping from the source.
- Asked whether the destination host is active.
- Asked to perform traceroute to the destination to check where the packet is dropped.
10) Can I request for an IP in the discover process?
No. We cannot request for an IP.
11) You have 2 PC connected to a switch with different VLAN and your dhcp server is multiple hops away, based on what parameter it will assign IP from its pool?
Based on the network address.
12) What is TCP half open connections?
A half-open TCP connection is when one side of the established connection has crashed, and did not send notification that the connection was ending.
13) Difference between RIP v1 & RIP v2?
a) RIPv1 is a Distance-Vector Routing protocol.
b) RIPv1 does not support VLSM (Variable Length Subnet Masking).
c)RIPv1 support maximum metric (hop count) value of 15. Any router farther than 15 hops( infinity) away is considered as unreachable.
d) RIPv1 routing updates are sent as Broadcast traffic
a) RIPv2 is a Hybrid Routing Protocol. A Hybrid Routing Protocol is basically a Distance-Vector protocol which some characteristics of Link State routing protocols.
b) RIPv2 support VLSM (Variable Length Subnet Masking).
c) RIPv2 support maximum metric (hop count) value of 15. Any router farther than 15 hops away is considered as unreachable.
d) RIPv2 routing updates are sent as Multicast traffic
14) What do you mean by routing update?
Each and every router updates its table which has network ID, interfaces after the Timer expires. This timer controls the interval between routing updates. The update interval is set to 30 seconds, by default, with a small random amount of time added when the timer is reset. ... The default value is 180 seconds.
15) A transfer was going on from PC2 to PC1, what will happen if the ARP table in L2 is flushed out?
The packet will be dropped.
16) What is INFORM message used for? List some other than NetBIOS, Win server
If the client is requesting for certain parameters (255) and not all the parameter requested by the client is replied by the server in that case it sends a Inform message.Other than NET bios and Win server it also request DNS, gateway lease time, Rebinding Time, Renewal Time,Static Route,Router Discovery etc.
17) What is renewal & rebidding time in DHCP?
In DHCP the default lease time for the IP is 8 days.
Renewal- Once it completed 50%, it send a request message to the server to get the same IP. If there is no reply from the server, the PC, still use the same ip until the lease time expires.
Rebinding- Once it come to 87.5%, client agan send a request to the server to refresh the shcp table to use the same IP.
If the server still not respond and lease time expires, it again do a DORA process to get a new IP.
18) Why first ping request fails?
The reason the first ping usually fails is that the remote router in that LAN has to put the ping request on hold to send out an ARP broadcast to learn the MAC address of the remote device, then wait for a response, and then send the first ping through. This delay is usually too long.
19)A switch with 10 ports and 2Lan has been assigned with 5 ports each. How many broadcast domain and collision domain?
Broadcast domain- 2
Collision domain- 10
20)If a router is getting a broadcast message, what will it do?
It check the the destination IP address and check their own routing table and forward the packet to the nest hop.
21) Can we connect Trunk link to server PC?
No- Trunk link is used to connect two switches and exchange the same vlan information.
22) After control connection, in data connection packets are getting dropped continuously. What are all the possible issue?
- FTP server in the WAN and behind the firewall is blocking.
- Maybe the Natting is not happening.
23) STP – Variant different types
STP – Variant different types
IEEE 802.1D PVST per VLAN spanning tree
IEEE 802.1W rapid spanning tree protocol (RSTP)
IEEE 802.1S Multiple spanning tree protocol (MST)
24) In TCP connection establishment, SYN is sent and Rest is received. Why?
- Due to port number is not supported.
EG: Ftp request send to the HTTP server, server do reset.
16. What is INFORM message used for? List some other than NetBIOS, Win server?
17. What is renewal & rebidding time in DHCP?
18. Why first ping request fails?
19. A switch with 10 ports and 2Lan has been assigned with 5 ports each. How many broadcast domain and collision domain?
20. If a router is getting a broadcast message, what will it do?
21. Can we connect Trunk link to server PC?
22. After control connection, in data connection packets are getting dropped continuously. What are all the possible issue?
23. STP – Variant different types
24. In TCP connection establishment, SYN is sent and Rest is received. Why?
SACK
A Selective Acknowledgment (SACK) mechanism, combined with a selective repeat retransmission policy, can help to overcome these limitations. The receiving TCP sends back SACK packets to the sender informing the sender of data that has been received. The sender can then retransmit only the missing data segments.
Explain DNS query process. a). When we open web browser and enter www.google.com in the address field. At that point, the computer doesn't know the IP address for www.google.com, so it sends a DNS query to the ISP's DNS server (The DNS server address is obtained by the use of DHCP). b). The ISP's DNS server doesn't know the IP address for www.google.com, so it will ask one of the ROOT DNS servers. c). The ROOT DNS server checks its database and finds no entry for google.com, but, it does know where to forward the local DNS server. d). The local DNS sever now contacts the TLD which is TOP Level Domain. The TLD has the domain names of top level domains such as .com, .org, .net and so on. The TLD still doesn't know the IP address of google.com. Hence, it forwards the DNS query to the next and final level. e). The local DNS server now contacts the Authorative Name server which knows everything about the domain name which includes the IP address. The ANS now directs to the google's DNS server to get the IP address of google.com. f). Google's DNS server checks its database and finds an entry for www.google.com. This entry has an IP address of 8.8.8.8. Since the IP address of the DNS server and webserver (www) are identical, this means they are likely to be both on the same physical server. g). Your ISP's DNS server now knows the IP address for www.google.com and sends the result to our computer. h). Our computer now knows the IP address of google's website and is able to directly contact it. Naturally, the next step is to send an http request directly to google's webserver and download the webpage. 11) Explain Iterative & recursive query Iterative Query :Iterative DNS queries are in which a DNS server is queried and returns an answer without querying other DNS servers, even if it cannot provide a definitive answer.Server Uses both iterative and recursive query Recursive Query:Recursive DNS queries occur when a DNS client requests information from a DNS server that is set to query another DNS servers until a definitive answer is returned to the client. The queries made to subsequent DNS servers from the first DNS server are iterative queries.PC always uses Recursive Query.
TCP HEADER
Address Resolution Protocol (ARP)
Address Resolution Protocol (ARP) is a required TCP/IP standard defined in RFC 826. ARP resolves IP addresses used by TCP/IP-based software to media access control addresses used by LAN hardware.
How ARP resolves media access control
addresses for local traffic ?
If the ARP cache has the information about host B ,then Host A will generate an ICMP ping request and send it to Host B and will wait for the ICMP ping Reply. But if the ARP cache does not have any information about HOST B then the 2nd step starts. Step 2: As ARP cache does not have Host B's Information. Host A will do an AND operation using the IP address of HOST A and IP address of HOST B in order to determine whether HOST A and HOST B are on the same network or not..HOST A considers the subnet mask configured on its machine. Eg. HOST A IP 10.0.0.1 Subnet Mask 255.255.255.0 00001010 00000000 00000000 00000001 11111111 11111111 11111111 00000000 00001010 00000000 00000000 00000000 10.0.0.0 is the Subnet address for Host A HOST B IP 10.0.0.2 Subnet Mask of HOST A 255.255.255.0 00001010 00000000 00000000 00000010 11111111 11111111 11111111 00000000 00001010 00000000 00000000 00000000 10.0.0.0 is the Subnet address for Host B
After ANDing process HOST A determines that both the HOSTS are on the same subnet.
Step 3: Now HOST A would generate a ARP Query Request which is a Layer 2 broadcast message and transmit it in its subnet. The ARP broadcast packet will have the following details in the ARP packet
1. The Source IP of HOST A 10.0.0.1
2. The Source MAC address of HOST A which is A (for our reference)
3. The Destination IP of HOST B 10.0.0.2
4. The Destination MAC address would be 00:00:00:00:00:00
[ note: The Layer 2 broadcast Address will be ff:ff:ff:ff:ff:ff ]
After ANDing process HOST A determines that both the HOSTS are on the same subnet.
Step 3: Now HOST A would generate a ARP Query Request which is a Layer 2 broadcast message and transmit it in its subnet. The ARP broadcast packet will have the following details in the ARP packet
1. The Source IP of HOST A 10.0.0.1
2. The Source MAC address of HOST A which is A (for our reference)
3. The Destination IP of HOST B 10.0.0.2
4. The Destination MAC address would be 00:00:00:00:00:00
[ note: The Layer 2 broadcast Address will be ff:ff:ff:ff:ff:ff ]
•The Internet Control Message Protocol (ICMP) is a companion to the IP protocol & has been designed to compensate for below deficiencies
§ The IP protocol has no error-reporting or error-correcting mechanism
The IP protocol also lacks a mechanism for host and management que
No comments:
Post a Comment